Think Your SOC 2 Struggles are Behind You? Watch Out For This Hidden Risk
Anecdotes’ 2025 State of Enterprise GRC Maturity research found a curious irony about GRC maturity.
In most respects, a mature GRC program justifies confidence. Your team has figured out reporting. You’ve evolved from traditional automation to AI. The stress of SOC 2 is safely in your rearview mirror.
Or is it?
As it turns out, the biggest and most mature GRC programs have a surprising blind spot when it comes to SOC 2 — a hidden risk that smaller and less mature GRC programs are actually less likely to miss.
To understand SOC 2 today, you have to know SOC-in-a-box
SOC 2 sprang from the best of intentions: establishing standards for safe handling of customer data. But over time, market pressure and shortcuts chipped away at those intentions.
SOC 2 is meant to be a rigorous process. Earning that AICPA “badge” can open doors to new customers and partnerships, but getting there should take real work. Building a solid security and compliance foundation takes time, and a thorough audit does too.
That effort used to set a high bar for entry. Then came the shortcuts.
Some vendors and auditors saw a business opportunity in promising fast, cheap SOC 2 outcomes. They started bundling lightweight tooling with a quick-turn audit, offering a one-size-fits-all approach that prioritized speed over substance. We call these offerings “SOC-in-a-box.”
To some, that sounds like democratization. And if all SOC 2 reports were created equal, we’d agree. But they’re not. Some auditors sign off with minimal scrutiny, so it’s hard to tell the true value of a company’s SOC 2 report.
{{ banner-image }}
SOC 2 myths are rampant among GRC professionals
At Anecdotes, we staunchly believe SOC-in-a-box is a dangerous commoditization of a process that businesses should take more seriously. We’ve been vocal about the dangers of SOC 2 for a while now. Making the SOC 2 audit process faster, cheaper, and easier was a slippery slope to devaluing SOC 2.
Unfortunately, our State of Enterprise GRC Maturity report shows that not everyone is aware of the dangers yet. Among all surveyed GRC professionals, 81% either somewhat or strongly agree that “SOC 2 certification is a sign that a company has good security practices.”
The vast majority also reported having a totally or mostly positive impression of SOC-in-a-box solutions. The smaller portion of survey respondents who saw what we see—that these package deals devalue SOC 2 and create risk—tend to be smaller companies. As the target market for these products, they’re probably more familiar with what the tools actually offer.
But even large companies need to be on the lookout. If a partner or vendor’s SOC 2 shortcut leads to a breach of your customers’ data, you’ll be just as much on the hook for the fines, the fallout, and the reputational damage.
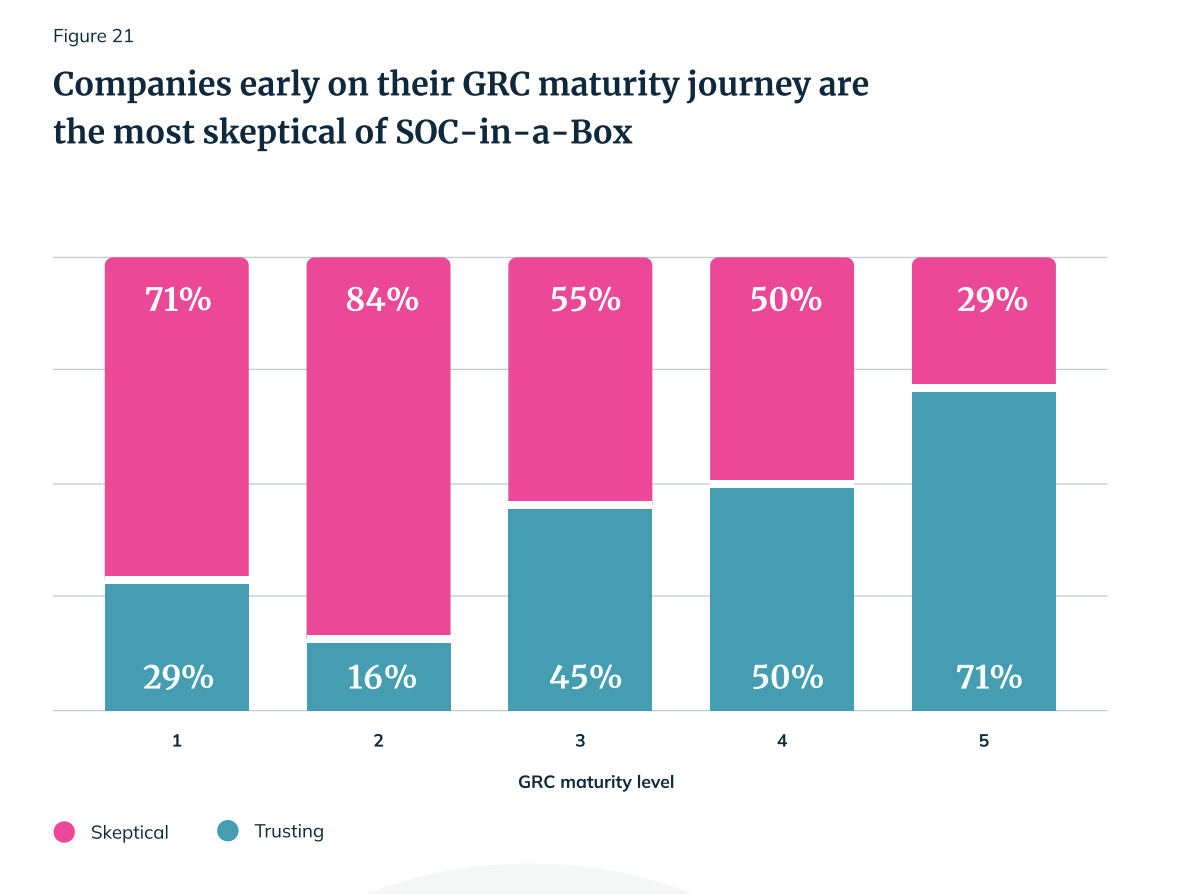
Survey says: Mature GRC programs have the worst blind spot
The situation gets even more worrying when we break out the survey results by GRC maturity. Paradoxically, professionals in the most mature GRC programs are most likely to assume that SOC 2 translates to robust security practices. Less mature teams saw less of a correlation.
Turning to SOC-in-a-Box, survey data shows us that the target audiences for these options — the smallest companies and those at the start of their GRC journey — are the most skeptical of them. We suspect this is because they’re actively researching or using these SOC 2 packages and see them for what they are.
But the most GRC-mature organizations are much more trusting of SOC tool + audit packages — not because they’re naive, but likely because they’ve had no reason to keep up with evolving “solutions” for a problem they’ve already solved.
Open your eyes to third-party risk in your value chain
SOC-in-a-box and the resulting devaluation of SOC 2 create a new kind of third-party risk. Ironically, bigger and more GRC-mature companies are the most likely to overlook it.
The lesson here is that even if you’re confident about how you’re driving your program, your partners or vendors could be tempted by SOC-in-a-box, and that would leave you open to vulnerabilities.
It’s a risk even the most mature GRC programs need to acknowledge and manage with due diligence. Next time you’re reviewing a SOC 2 report, ask yourself these questions:
- Does the report indicate a thorough and in-depth audit?
- Who issued the SOC 2 report? Are they reputable?
- What additional information can you examine besides the report?
You’ve built a mature, data-driven GRC program. Don’t let someone else’s shortcuts become your liability.
Curious about what GRC maturity looks like at other organizations? See how your team stacks up in the Anecdotes State of Enterprise GRC Maturity report. Download your copy now.


.png)

.png)
.png)












.svg)
.svg)
.svg)

